A access management system allows departments to assign access permissions to directories and sites themselves.
This improves data security, accelerates clearance processes, and relieves the burden on IT resources.
Huge volumes of unstructured data in the form of documents – often with highly sensitive content – are stored on file servers and SharePoint in many organizations. The risks involved mean this kind of data storage is especially susceptible to abuse: After all, passing on file-based data is no challenge – even for non-techies.
So it’s all the more important to keep the number of people with authorized access as low as possible. At first, this task may not sound particularly difficult. But there are ample technical possibilities for restricting directory access at the level of various operating and directory systems.
Legacy Structures
In practice, the complexity of this task can be seen increasingly in the requirements of departments for nesting in the permission structure, uninterrupted inheritance, the creation of crosslinks, and the often ad-hoc assignment of direct permissions to individual users despite carefully thought-out group concepts.
Ultimately, most adjustments are made in line with the organization and existing business process, but they sooner or later result in a barely comprehensible permission structure. It’s no wonder that most data controllers with only limited technical expertise tend to lose track in these structures.
But how do these situations arise? The cause is typically a combination of permission dialogs aimed at technical users, countless configuration options, manual errors in assignment of permissions, and finally a lack of complete documentation. In many cases, it is no longer possible to quickly and reliably determine who can access which data – and above all: Who approved this access at what time?
Analyzing and Restructuring – but what next?
Existing analysis tools give organizations the ability to gain an overview of their current permission structure, as well as to analyze, restructure and simplify it. But how can permanent reproducibility be ensured with constant changes to the organizational structure, functional areas, and responsibilities?
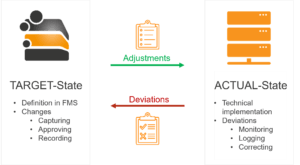
The constant challenge is in seamlessly recording this ongoing change process, while also making sure that the actual technical situation matches the approved target state and that it can’t be circumvented.
The key to audit-proof access management therefore lies in the combination of extensively automated permission processes, from requests to implementation, continuous monitoring, and comprehensive reporting. All of which are the core competencies of the BAYOOSOFT Access Manager.
The triggers of adjustments to the permission situation can be the users and data controllers directly via the Self-Service Portal or another system via API, depending on the situation and operating environment. Coupled with a continuous comparison of the actual permissions with the state defined by data controllers, this solution results in unprecedented transparency regarding granted access permissions.
The aim of automated permission assignment via self-service is to shift the responsibility and handling of permission processes away from administrators and toward data controllers. After all, only when permissions are no longer assigned “outside the system” but exclusively via the prescribed application and clearance workflow, is it possible to sustainably maintain the defined target state and prevent unauthorized access. This also reduces the workload on IT administrators and the helpdesk.
Ongoing monitoring
The automatic comparison of the actual permission situation with the defined target state as well as the automatic reversal of “unauthorized changes”, where necessary, strengthens data protection and prevents uncontrolled growth in the permission structure. By involving the responsible controllers in the permission process and with the associated transferal of responsibilities, greater awareness is achieved among the relevant decision-makers when handling the assignment of access permissions to “their” directories, significantly increasing data security.
Transparency
The use of the BAYOOSOFT Access Manager secures the permanent reproducibility of all decisions: The permission situation is continuously monitored and every permission change is logged in an audit-proof record. Simple analysis reports that are easily understood without IT know how can be created at the touch of a button, providing maximum transparency for data controllers and hence an important contribution to the organization’s information security. Data controllers are thus able to obtain an overview at any time: Who has access to which data, since when, and who approved this access?
Summary
Solutions for automated access management offer far more than a visual interface as a replacement for often complicated standard dialogs in the operating system or cryptic reports. Using these kinds of products provides a sustainable system for transferring the assignment of permissions from IT administration to the data controllers, wherever this seems appropriate. They also enable non-technical data owners to participate in the permission situation thanks to the simple transparency. The continuous comparison of the actual and target situation enables a permanently clean permission structure. Involving the data controllers sustainably leads to greater awareness in the handling of access permissions and thereby increases information security. When considering the introduction of a access management system, organizations often have a choice between a holistic identity and access management (IAM) solution or a specific solution according to the best-of-breed approach. The best-of-breed approach is typically the best choice especially in environments with a high need for protection. It places an restricted focus on file server and SharePoint permissions, and even complex permission structures can be monitored down to the level of the technical resource. The BAYOOSOFT Access Manager offers modular expandability and can be adapted to various requirements. A REST API is available as an expansion module for integration in workflows and other IAM systems.
Would you like to learn more about the advantages of automated access management?
Arrange an appointment for an individual product presentation today or drop by one of our open webinars. Our access management experts will be pleased to present the BAYOOSOFT Access Manager to you personally.