Redundant monitoring in access management
Sensitive data with peace of mind
Assigning permissions to file servers, SharePoint, Active Directory, and items in third-party systems takes up a range of operating resources. The extensive automation of access management can significantly reduce these expenses while also increasing data security and transparency.
Following the need-to-know principle, a user should only receive as many permissions as they require to fulfill their current tasks. In practice, however, more and more extensive permissions accumulate over time, although most may no longer be needed. Existing permission systems may not even allow a clear delineation of permissions – or they over-simplify to reduce the manual maintenance required. The Access Manager closes the gap between the seemingly contradictory objectives of ensuring data security while keeping maintenance low.
This is where the Access Manager comes in with the integrated Reapproval system. This process also benefits from intuitive use via a browser, enabling straightforward and transparent access management.
- Information about pending reapprovals by email
- Clear presentation of the necessary information
- Intuitive decisions
- Reminders raise awareness
- Simplification through status reports
This way, the recertification process is made as simple as possible for data controllers. They’re neither confronted by mountains of paper nor unfamiliar IT details, allowing them to perform the task effectively. The option to set multiple data controllers per resource also allows the work to be spread among several people.
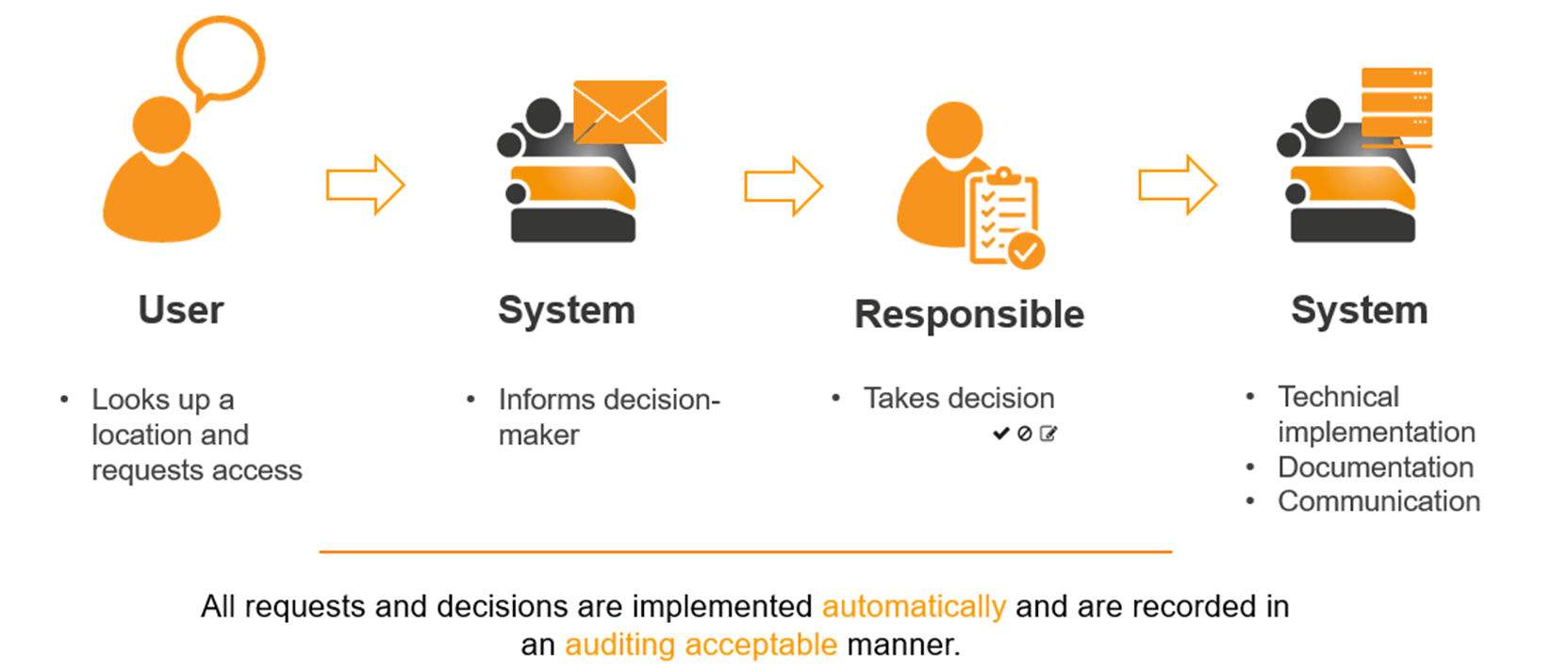
Automating access management is the key to achieving time and cost savings in operation, preventing manual errors, and increasing data security – one of the core principles of the Access Manager. From interactive user requests via the Self-Service Portal (or via an assistance function) and the identification of the responsible decision-makers (or a representative), to audit-proof decision documentation and the implementation of technical changes – the Access Manager handles access management without any involvement of the help desk or IT administrators.
With our many years of expertise regarding heavily regulated sectors and critical infrastructures in enterprise environments, we attach great importance to complying with current legal provisions in ongoing development. For this reason, it goes without saying that we ideally support your processes in complying with the General Data Protection Regulation (EU GDPR 2016/679) with the Access Manager.
For instance, the software solution offers the option to mark resources that contain or process personal data and to define a purpose of processing. This functionality can be effectively combined with additional features, such as the recertification process or a clean-up function to remove data no longer required in accordance with the prescribed deletion periods.
Data controllers are thus able to obtain an overview at any time: Who has access to which data, since when, and who approved this access?